
Cyber Resilience Program
Cyber Security Program
Your cyber security program must be built to provide cyber resilience across the business. Achieving this means that you will need to follow a process of discovering the areas of risk within your business and understanding what can be done to protect these.
Cyber security is such a big risk and covers so many different points that many businesses have no idea where to start. The mere thought of the different types of risk and many areas of concern seem insurmountable and they therefore do nothing and pretend the risk isn’t there. Unfortunately, if you ignore it - it does not go away.
The key is to build your organisation’s own cyber security program and the most important part of the journey is getting started. Using a Unified Security Management (USM) approach and ensuring you work towards achieving continuous improvement by building cyber resilience into the very DNA of your business will guarantee cyber security maturity improvements. Nothing will get better if you do not get started.
Building cyber resilience into the DNA of every business is at the heart of the J2 approach. With improved visibility, managed solutions and continuous monitoring we can help you understand what is happening, identify problems as soon as they occur and allow you to rapidly remediate any issues. Cyber resilience does not mean that you will never have an incident; cyber resilience ensures that when you do, it will not destroy your business and you can continue to operate without suffering any losses.
Continuous improvement is an ongoing process and by starting with the basics and using modern, managed cyber services we will help you build your security program as strategic partners to your business. J2 provides you with a diverse team of experts that are looking after the security of your business. We will expand your capacity, provide the ability to identify and detect risks, introduce the capability to respond to threats and ensure that you can recover in the event of an attack. Cyber resilience is for everybody; no matter the size of your business.
2 CSC delivers next-generation security today and provides managed security for every business. There is no one-size-fits-all solution. We work to ensure that your requirements are met and security gaps are covered so you can focus on your business.
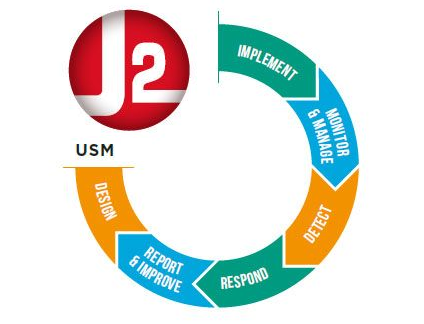
J2 CSC Unified Security Management
J2 has developed a layered security approach, using inputs from various globally accepted security frameworks, to provide real and practical security for every business. Not every business will want to, or be able to, achieve ISO27001 certification or have a legal obligation to comply with specific data security and compliance regulations, but it is still a great idea to use the practical aspects of programs such as these to ensure a comprehensive, affordable and real cyber security program is deployed within your business.
We understand that the adoption of a formal program will differ from business to business, however the basics remain the same. Using our approach to practical security for your business it is important to break down the key areas of risk to IDENTIFY what it is that you will be securing. These categories can be described as follows:
USERS
The users are the biggest area of risk within any business. This is because the users and associated user accounts have access to data and systems. Securing the user is a critical aspect and overlaps into every other area that requires protection including email, data, machines, systems and the internet. The user is the weakest link in the security chain, not because they are inherently risky, but because their access can be exploited to breach systems. Users touch all systems and devices across the business. For example, the user requires secure access to systems and needs the ability to interact with data, the internet, other machines and people. J2 recommends a user-centric approach to security rather than maintaining a network focus because in the modern workplace the network no longer exists. Your network is wherever your users are.
The most intrusive of all business systems in the modern workplace is email and other collaboration tools. Email is often used to process orders, confirm bookings or send invoices and provides almost immediate capability to service your customers. Email is also the most targeted method of attack by cyber criminals. Using email, social engineering and targeting your users; cyber attackers will take advantage of any misconfiguration or security gap to get hold of your data and systems. This collaboration now extends further to cloud and online platforms where your sensitive and financial information resides. Your cyber security program must incorporate visibility and protection of the tools used in the modern workplace to ensure their security. Cyber resilience for email is a pivotal component of the cyber security program and overlaps with user, data, machines and internet portions of your risk profile.
DATA
The lifeblood of any business in the modern age. Data is the new oil. Data is your competitive advantage and losing this edge can lead to major losses and even closure. Protection of data, wherever it resides or wherever it moves is key in a layered and comprehensive security program. Cyber resilience requires data management to extend beyond access only. In order to ensure secure availability of data you will also need to incorporate encryption, access controls, monitoring and effective backup. A lost laptop or hard drive should not mean a loss of competitive advantage or require the notification of the Information Regulator. Cyber resilience for data gives you the peace of mind that when data is deleted, misplaced or encrypted you have control over the restoration. We will also work with you when it is time to forensically delete data from hard drives or old machines. The protection of information is not only critical to business operations, it is also a vital part of compliance. Deploying practical and affordable data protection can be achieved.
MACHINES
Everything is inter-connected and the machines that access your systems and data are a vital cog in the machine. Inadequate control and security of the devices that access your data will leave massive holes in your security posture. Cyber resilience is driven through the program by ensuring that your machines are all encrypted, access is controlled and the data and machine itself is visible and updated. Incorrect and unmanaged access can have a devastating impact on the business, but with a layered and integrated cyber security program you will have cyber resilience built into the everyday operation of the business without impacting performance.
INTERNET
The big connection. The highway that allows all aspects of the modern workplace to happen. Your users access it to collaborate, learn and share. Email traverses it and data moves across it. Your systems and machines use it to store, process and manage information. Your customers use it to stay in touch with you and cyber criminals live on it, waiting to discover the opportunity to attack you over it. There is no getting away from the connected world and cyber resilience, in our connected spaces, means we will require safe, secure, managed and monitored access to the internet to stay in business. Inline, unobtrusive protection and visibility has to be allowed. Applying the principles of cyber resilience and making sure you have maximum visibility will allow you to identify problems before they become a full blown breach.
Cyber resilience and a comprehensive cyber security program is possible. J2’s proven approach of getting things done with simple, practical, effective and managed cyber security solutions will put you on the right track.

-
INSIDER THREAT
-
WORKFORCE CYBER INTELLIGENCE
-
USER PRODUCTIVITY
-
USER AWARENESS TRAINING
-
EMAIL CYBER RESILIENCE
-
MICROSOFT 365
-
SECURE HOSTED SERVICES
-
SECURE OFFSITE BACKUP
-
RANSOMWARE PROTECTION
-
DATA DESTRUCTION
-
END-POINT PROTECTION
-
PATCH MANAGEMENT
-
DEVICE & APP CONTROL
-
MFA & ENCRYPTION
-
WEB SECURITY & DNS PROTECTION
